
It’s no secret that the fashionable workforce relies on a myriad of apps to perform practically all of their function. From movie conferencing to doc collaboration, quick messaging, and CRM, the record goes on and on. No matter of the place these apps are hosted, employees have to have seamless, superior-efficiency obtain to all of them.
Security practitioners are tasked with maintaining buyers, property, apps, and knowledge safe and sound. The assure of Zero Believe in Network Obtain (ZTNA) – supplying access for a user to an application relatively than wide access to a community – is intended to enable relieve the difficulties of accomplishing this. Nevertheless, as I reviewed formerly, the implementation of ZTNA 1. has elementary flaws. In addition to those described formerly, ZTNA 1. fails to empower regular safety because it only works with a subset of apps that the organization depends on.
ZTNA 1. Is Unable to Protected All Applications
The vision of regular, great-grained access to all programs just cannot be accomplished with ZTNA 1.. That’s because ZTNA 1. remedies do not secure all applications. They really don’t assist cloud-centered apps or other applications that use dynamic ports or server-initiated purposes – like assist enable desk applications that utilize server-initiated connections to remote devices. ZTNA 1. alternatives really do not assistance SaaS apps, either.
Modern-day, cloud-indigenous apps are typically comprised of several containers of microservices, frequently working with dynamic IP addresses and port quantities. Implementing ZTNA 1. for this sort of software is a recipe for disaster. ZTNA 1. becomes completely ineffective for these types of application constructs because it presents obtain to a broad selection of IPs and ports, exposing the organization to more hazard and defeating the issue of Zero Believe in.
As much more and extra companies go on on their cloud journey and operate their enterprises on cloud-indigenous purposes, ZTNA 1. will turn out to be obsolete.
ZTNA 2. Delivers Steady Security for All Apps
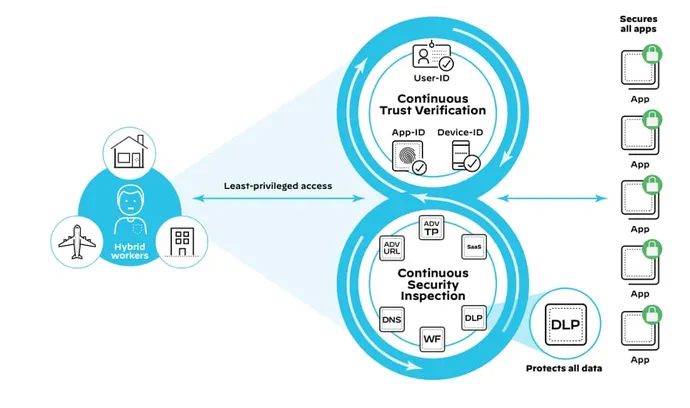
Though legacy ZTNA options only deal with a portion of enterprise applications, ZTNA 2. will protected all applications, regardless of where they’re hosted. It can be a present day cloud-indigenous microservices-based application that does not get restricted by IPs and ports, a SaaS application, a conventional private app or legacy application.
ZTNA 2., shipped by Prisma Access, provides exceptional security whilst offering uncompromised effectiveness and extraordinary person encounters, all from a solitary unified strategy. It is objective-built on a actually cloud-indigenous architecture to protected today’s electronic enterprises at cloud scale, offering uncompromised overall performance backed by major SLAs that produce fantastic user working experience. Being completely software program-primarily based and hardware neutral, car-scaling enables Prisma Entry to maintain up with transforming hybrid workforce and evolving enterprise calls for with no demanding guide interactions or procedures.
ZTNA 2. Is Zero Believe in with Zero Exceptions
Pursuing a real Zero Trust posture is a journey, and delivering reliable safety and regulate throughout all apps, no matter of where they are hosted or accessed from, is an essential phase. Which is why securing all apps employed in the organization, which includes modern applications and SaaS, is a main pillar of ZTNA 2..
To discover more about how you can protect your business with ZTNA 2., be certain to watch our ZTNA 2. digital function, in which we explore improvements and best methods for securing the hybrid workforce.

Kumar Ramachandran serves as Senior Vice President of Merchandise for Secure Access Service Edge (SASE) merchandise at Palo Alto Networks. Kumar co-launched CloudGenix in March 2013 and was its CEO, establishing the SD-WAN classification. Prior to founding CloudGenix, Kumar held management roles in Products Administration and Internet marketing for the multi-billion dollar department routing and WAN optimization organizations at Cisco. Prior to Cisco, he managed applications and infrastructure for firms these as Citibank and Providian Economic. Kumar retains an MBA from UC Berkeley Haas Faculty of Company and a Master’s in Laptop or computer Science from the University of Bombay.








